Hacking Package Pickup
Just over a week ago my apartment complex launched their new "Package Pickup Center" - an automated locker system much like those that Amazon and others are using to allow 24x7 collection of packages. Like all of these systems, it consists of a number of computer-controlled lockers, and a screen where you can enter a code sent via email that will unlock the relevant locker.

Given that I was expecting a package, a few days ago I decided to go and check it out.
After tapping the touchscreen to wake it up, it displays a very simple interface - one button to allow you to enter a code to pickup a package, and a smaller button down the bottom if you're a courier dropping of a package (which then prompts for a username/password).
There's also a logo for "TZ" who appear to be the vendor for the system - according to their website they are the "The SMArt Devices and SMArt Systems Leader" (I'm not sure if the capitalization is supposed to means they are only 3/5th smart or what?)
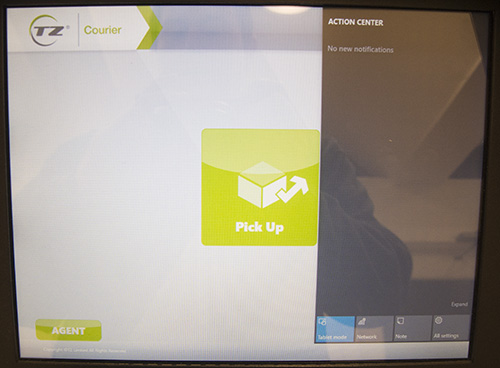
Of course, I'm not one to stick to the available buttons, so I tried clicking and dragging in a few random locations, and sure enough within a few seconds I had broken out of the "captive" screen and had what was clearly a Windows Action Center window.
A few more gestures and I had the full Windows desktop, complete with Twitter updates, Minecraft, and an incorrectly set clock.

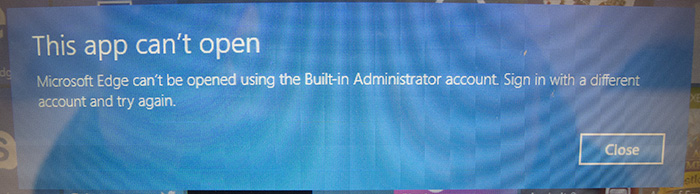
In an attempt to check that I had Internet access (which given the system sends automated emails I was pretty sure it would have), I tried to fire up Microsoft Edge. The good news is that it blocked me. The bad news is why it blocked me...
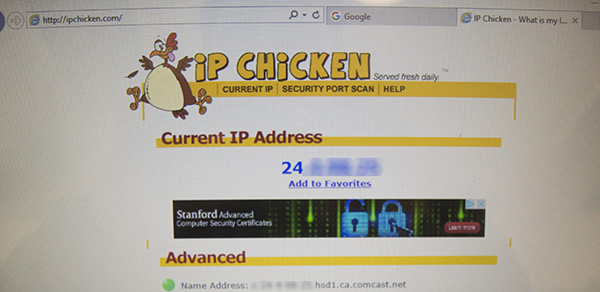
Not surprisingly, Internet Explorer did work, and showed that it did indeed have Internet access via a Comcast Xfinity connection.
A quick look around the filesystem resulted in a log file for the TZ software, which showed that SQL Express was being used for at least some part of the system.
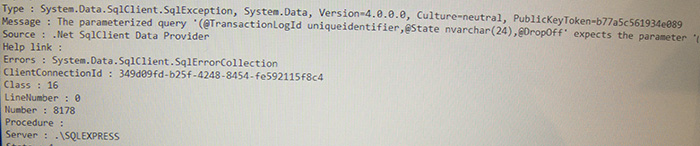
Also on the desktop was a CSV file containing the names, email addresses, apartment numbers and phone numbers for all of the residents in the apartment complex.
Given that SQL Express was being used, it wasn't surprising to find that SQL Server Management Studio was installed, nor that it was configured to use Windows Authentication so no password was required.
The schema was fairly simple, so it didn't take long to find the details of all packages that the system had handled, including who they were for, when they had been delivered, and for most of them when they had been picked up - plus the Pickup Code that had been assigned to them.
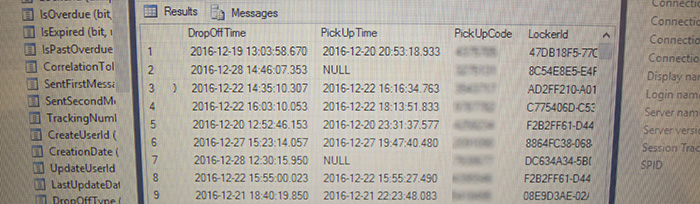
Querying instead just for those without a pickup time found the 20 or so packages that were ready for pickup. At this point it would have been a trivial exercise to grab their Pickup Codes, enter them into the application, and take the packages.
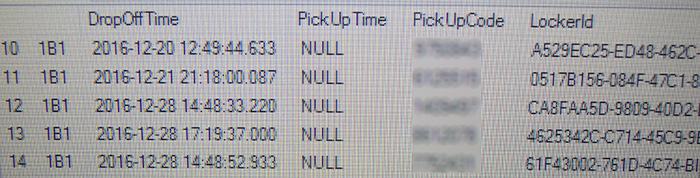
Not surprisingly, the database also contained the same details for all residents that had been in the CSV file above - name, apartment, email and phone number.
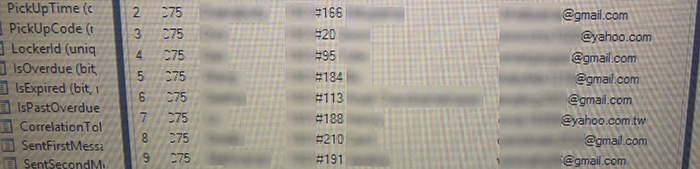
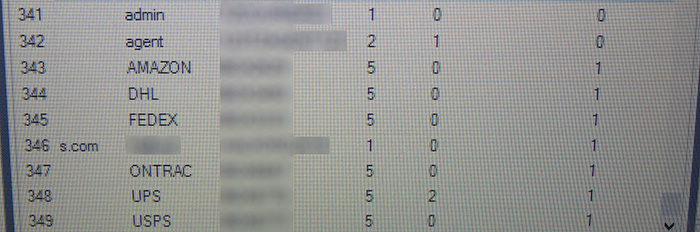
The same table also contained a number of users with cleartext passwords - no doubt the accounts used by the delivery companies to drop packages, as well as a few admin-style accounts (those with "1" in the column after the blanked out password), including one that had what was fairly clearly a default password still set.
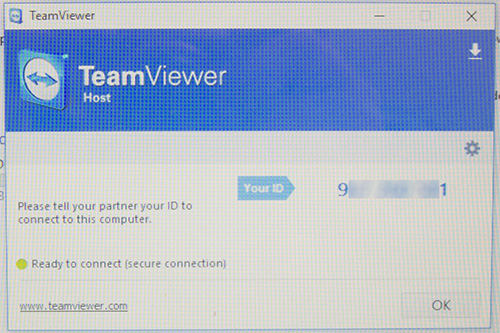
The one place that the system did appear to have any security in place was the copy of TeamViewer Host that was installed - which had a password configured. However given that TeamViewer allows multiple static password to be configured it would have been trivial to add an additional password to claim full remote access to the system, in a way that almost certainly would never have been noticed.
The good news is that a few days after alerting my apartment complex management the to issue they do appear to have fixed the problem. The ability to get out of full-screen mode is gone, which I can only hope was done using Windows Kiosk Mode so it might actually be secure.
If I had to guess, I'd say that the system was actually configured to be secure, but in setting it up one of the users manually started the kiosk app (whilst logged in as admin rather than the kiosk user) and then forgot to close it down and start it properly - although that's no more than a guess...