United Airlines Mileage Plus/Points.com Information Disclosure
(Update: Less than 24 hours after posting this blog entry United Airlines fixed the problem described, and a password is now required to access the site in question. It's a pity it took over 18 months and eventually public disclosure to get the issue fixed, but at least it is now resolved!)
Ever left a boarding pass in the seat-back pocket on your flight? Or perhaps dropped it whilst on the shuttle to the rental car center? How about the baggage label on your checked bag - ever thrown that in the bin without a second thought?
I'm sure most of us have at some time, but would you do that if you knew that boarding pass or baggage tag allowed someone to access all of your Mileage Plus personal information, such as your home address, phone number, email address and even your Mileage Plus point balance, date you opened your Mileage Plus account, and whether or not you own a United-branded Chase credit card?
Of course, none of this information is included on the boarding pass, but due to an information disclose bug on one of United's partners websites, it's possible to access all of this information using only 2 pieces of information that are on every boarding pass - a surname, and a frequent flyer number.
(There is a second issue that allows you to also obtain this information using only the surname and ticket confirmation number, however United has at least committed to fixing this issue. As the confirmation number is also on the baggage tag it's possible to use that to get this information as well).
To their credit, several years ago United Airlines did start "masking" the frequent flyer number on boarding passes (eg, writing it as AB-***123), however every boarding pass still contains a large 2D barcode, which contains all sorts of interesting information about your ticket, including your full Frequent Flyer number (plus your surname, but that is printed in clear on the boarding pass anyway).
Armed with the Surname and Mileage Plus number, it's then off to one of United's branded websites that is actually run by points.com, buymiles.mileageplus.com As the name implies, this website allows you to buy additional Mileage Plus miles, or transfer them to family members. In order to "authenticate" to this website, the only details you need to enter are - you guessed it - a surname and a Mileage Plus number. Of course, this wouldn't be a problem if all you could do would be to purchase Miles (using your own credit card!) for the person you're logged in as - however as a part of the "login" process the website actually leaks information about the user whose details have been entered.
The first two piece of information are blatantly displayed on the post-login page - your current Mileage Plus balance, and a masked email address. Not good, but not too bad either.
The issue isn't so much with what is shown, as what isn't. During the authentication process, a number of other details are passed to and from the websites involved VIA THE BROWSER. This means it's simply a matter of looking at the data being passed to determine multiple other details about the account :
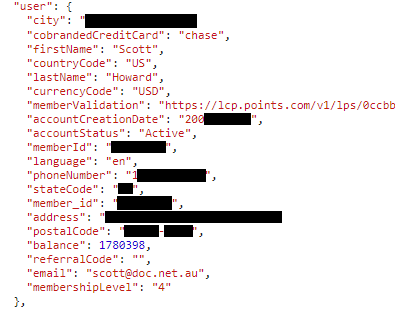
So very quickly we've gone from having only the users surname and Mileage Plus number (or even just their boarding pass!) to having their home address, phone number, whether or not they have a United credit card, the date their account was created, mileage balance, and their United Mileage Plus status (4=1K, 3=Platinum, etc).
If nothing else, this information would leave the the user open to a very targeted phishing attack - especially given that we also have details of a recent flight they took (based on the boarding pass).
Disclosure to United Airlines
This issue was reported to United via their "Bug Bounty" program in July of 2017. After spending around a week investigating the issue they responded that :
"After looking into the issue we have determined this finding is not a valid security concern. The values apparently are required for other service calls. They are transmitting the information securely."
It is now 18 months later and the issue has not been fixed.
The information disclosed is data that would be considered Personally Identifiable Information (PII) in most jurisdictions, and in particular would fall under GDPR in the EU, so it's a little hard to understand why United considered this not to be a "valid security concern".